Access Control on API Gateway
By default, API Gateway will accept all requests to your services. This means there will be a lot of malicious requests/attacks to your service and API Gateway is the role to “filter out” those and secure your infrastructure.
Zero Trust Model
Zero Trust Model means that all edge services does not trust/approve incoming requests, until it can prove/establish trust in the backend system
API Gateway supports Zero Trust Model by using “Authorizers”. They are considered as an “Interceptor” which check each request’s identification. API Gateway applies “Facade Design Pattern” to the authorization implementation so that the authorization logic can be abstracted away.
Not familiar wiht Facade Pattern? Check what I wrote before: Design Patterns: Facade Pattern
There are three type of autorization methods
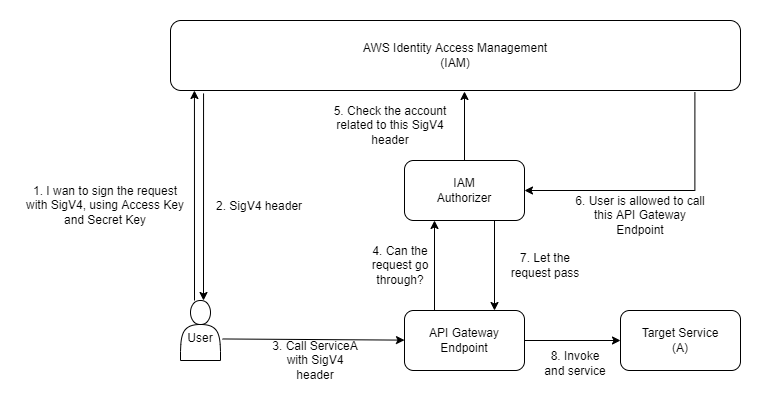
IAM Autorizer
The most intuitive way to authorize the request, by signing your request using SigV4 of your AWS credentials. API Gateway will go to IAm and verify the request identity and decide if let the request pass in or not.
AWS Cognito
In order to use Cognito for authorization, you must create a cognito user pool. Then you can use the Authorizer tab in API Gateway Console to select Cognito as the authorization method
- AWS Cognito return a JWT (JSON Web Token)
- User makes request to API Gateway with the JWT
Customed Lambda Authorizer
If you or your oganization already has the implementation of the Authorization, you can leverage Lambda (AWS Serverless Function) as the authorization implementation of your APi Gateway.
Lambda authorizer requires identity information coming from request, so
- JWT that passed along in the request
- Request header or request body contains the identity information
Infrastructure Security on API Gateway
Rate Limitimg
What is rate limiting and why we need it?
What Rate Limiting means on Wiki, here
In my opinion, it is a term that means that we “limit” the rate that this service can be accessed within a time unit.
Since API Gateway could serve as publicly facing, we should be aware of that our service could be suffered from a wider DDoS attack, which means a lot of traffic comes into your service and then if your server is not able to handle such many traffic, then it will “down”.
In order to prevent this to happen, API Gateway gives us the ability to “limit” the access to your service to two important parameters:
- Sustained request rate: average rate number which your application gets request over a time unit
- Burst request rate: same meaning as itself, this is a buffer which helps your application in case there is a large amount of requests comes in (request spikes), over a time unit
Token Bucket Algorithm is used by API Gateway team under the hood, to read more, here
If you want your Rate Limiting to be more fine-grained, there is also a stage-level or method-level rate limiting that API Gateway supports
Mutual TLS
This topic will be covered in more details in the upcoming post.
TLS helps validate the server uysing a standardized handshake and digital certificates signed by trusted certificate authorities for each domain.
mTLS asks each client to authenticate every request they sent in to increase the security level
mTLS is commonly used for B2B applications
Binary Files support
API Gateway also supports Binary Media files support, but you have to enable the configuration and re-deploy the gateway to make the change take effect.
- Binary Files as Input
- Binary Files as Output
- You should return a Base64 encoded String of the Binary files you wanna return and set the
isBase64Encodedtotruefrom the API output - Handling binary data using Amazon API Gateway HTTP APIs
- You should return a Base64 encoded String of the Binary files you wanna return and set the
