A.Networking for Applications
To continue our series on Terraform on AWS, we will now focus on networking.
The ${var.example} syntax is for including the result of an expression into a larger string. It is part of Terraform’s string template syntax. For example, you might write
${var.example}-foo
to produce a string that consists of the value of var.example followed by the literal suffix -foo.
If you need only the value of the variable in isolation, without concatenating it with any other string values, there is no reason to use that interpolation syntax:
var.example
${var.example} # are exactly equivalent.
For simple situations that Terraform can understand via basic syntactic analysis, terraform fmt will replace a redundant expression like
{var.example}
with its simpler equivalent
var.example
That tool encodes various idiomatic style conventions like this, and so it can be useful to apply the result of that tool (either directly by running it, or via its integration into plugins for editors like Visual Studio Code) to see if it makes an adjustment that would make your configuration style consistent with the usual idiomatic style.
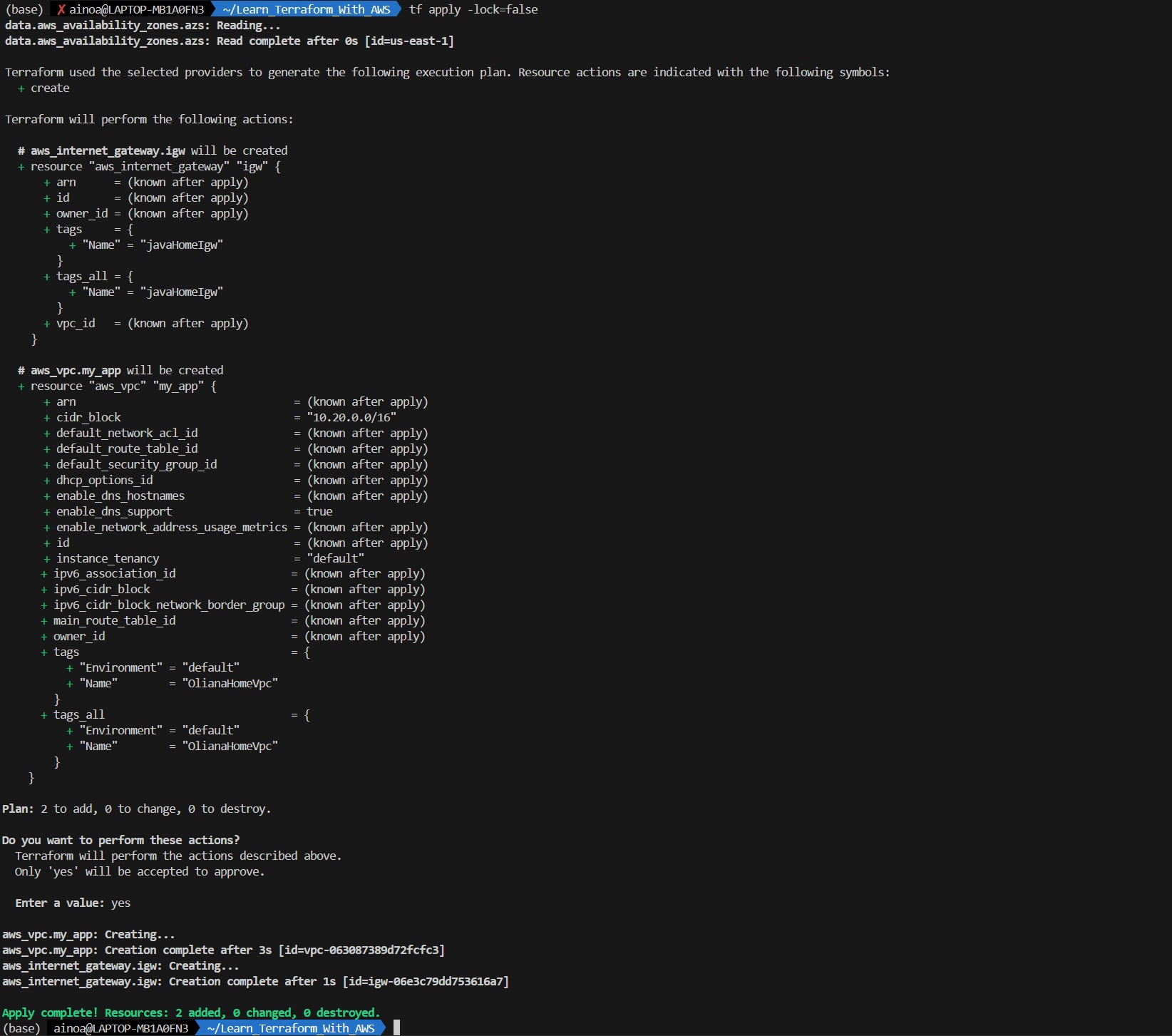
A.1 - Create Public Subnet
For High Availability we need multiple subnets spanning multiples availability zone. For making those subnets public, we have to create internet gateways (IGW) and configure them through route table.
- sh cidr_block = "${var.vpc_cidr}" : Returns the variable vpc_cidr define in variables.tf file.
- Variable define in
dev.tfvarsfile are variable that is use in command line and those variables overwrite the one define in different file.
resource "aws_subnet" "public" { # Define resource with logical type and logical name
count ="${length(local.az_names)}" # az_names is the list of the names of different az in the
# region we work in.
vpc_id = "${aws_vpc.my_app.id}" # Retrieve the Id of each VPC created
cidr_block = cidrsubnet(var.vpc_cidr,8, count.index) # Given a cidr_block, cidrsubnet will add 8 to a mask and
# return one by one.
availability_zone = "${local.az_names[count.index]}" # count.index is to pick one by one element in a list starting at 0
tags = {
Name = "PublicSubnet-${count.index +1}" # Here we will have for tags PublicSubnet-1, PublicSubnet-2, etc...
}
}
A.1.1 - Public subnet - Data Source CIDR Subnet
Data sources help us import some informations (metadata) with is define outside terraform configurations
We’ll use Data sources to fetch Availability zone from AWS account.
# Decare the data source
data "aws_availability_zones" "available" {
state = "available"
}
This return all availability zone based on the region we’re provisioning ressource.
When this Terraform configuration with appropriate provider settings is initialized and enabled, Terraform reads the information from AWS and makes it available in the data.aws_availability_zone.available variable.
To return all recent AWS AMI id from recent AWS, you can use:
data "aws_ami" "example" {
most_recent = true
owners = ["self"]
tags = {
Name = "app-server"
Tested = true
}
}
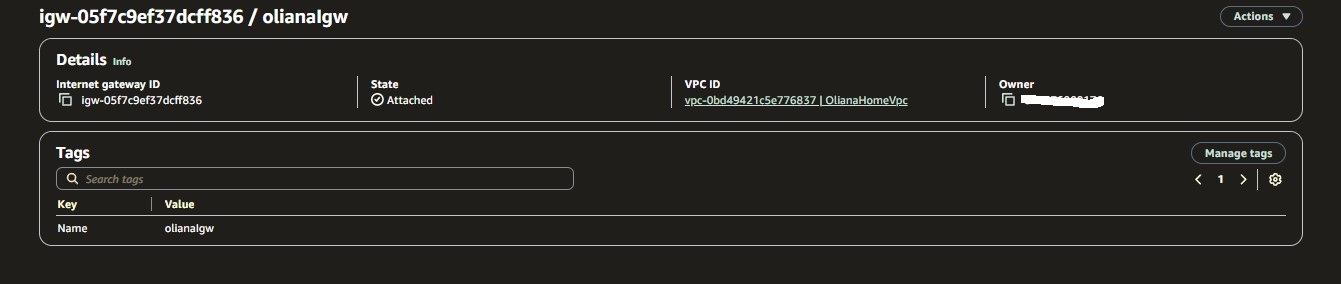
A.1.2 - Public subnet - Internet Gateway (IGW)
resource "aws_internet_gateway" "igw" {
vpc_id = aws_vpc.my_app.id
tags = {
Name = "Oliana-Igw"
}
}
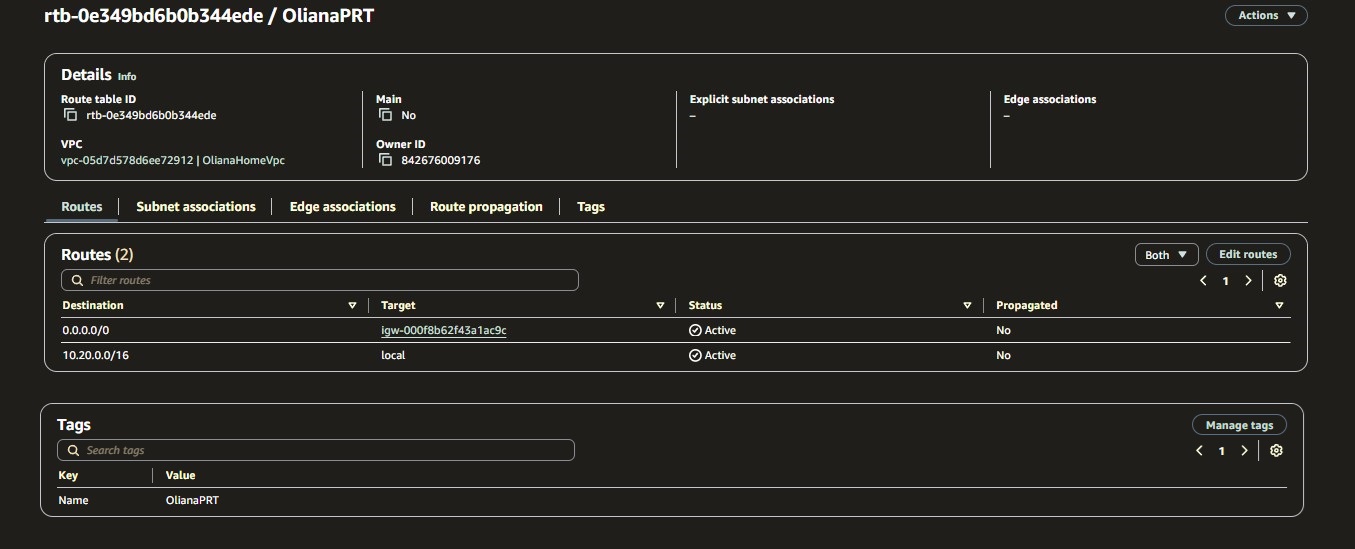
A.1.3 Public subnet - Route Table (Associate route table to internet gateway)
resource "aws_route_table" "prt" {
vpc_id = aws_vpc.my_app.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.igw.id
}
tags = {
Name = "OlianaPRT"
}
}